In taking a stand and making a direct protest against the death sentence handed in 2012 to a 17-year old teenager Mohammed al-Nimr, Anonymous has crippled multiple Saudi Arabian government websites. It is a case described as “a possible breach of international law,” by a group of UN human rights experts. Ali Mohammed al-Nimr was arrested and sentenced to death after being accused of partaking in pro-democracy demonstrations during the Arab Spring of 2012. At the time, Nimr was 17. In joining the international outcry against the sentence of execution by beheading and crucifixion, hacktivist group Anonymous has taken down multiple Saudi Government websites with an operation called #OpNimr. The hashtag has since gone viral and adopted by activists around the world. #OpNimr Anonymous announced #OpNimr by inundating government websites with DDoS attacks and taking them offline, along with the following video that demanded the release of Nimr. The statement released on the video said: Ali Mohammed al-Nimr, an innocent young teenage boy has been sentenced to death in Saudi Arabia and we will not stand by and watch. “Hundreds of innocent people die each year because of the Saudi Government, and they (the Saudi Government) will now be punished for their actions,” Anonymous said. Nimr’s final appeal against his execution was dismisbsed by Saudi courts in September 2014 for his part in attending a rally during the Arab Spring. At the time, a Saudi court judgement read: “[Nimr] encouraged pro-democracy protests [using] a Blackberry.” “Naturally, the sentence was appealed but the appeal hearing was held in secret and apparently dismissed,” added Anonymous in their video message. A second video was released by Anonymous days after their first, this time directly addressing King Salman and the Saudi Arabian Government. “13 judges have already approved the death sentence of Ali Mohammed al-Nimr, meaning only King Salman bin Abdulaziz Al Saud has to approve it,” Anonymous said. We cannot and will not allow this to happen. The Ministry of Justice was taken offline a few days ago, and we will continue to do this to other government websites. Some of the websites taken down include: The Ministry of Justice (saudinf.com) The Ministry of Civil Service (mcs.gov.sa) The General Administration of Education (tabukedu.gov.sa) Saudi Airlines (saudiairlines.com) A complete list of the targeted websites has been published by Anonymous in Pastebin, here. “We hope you listen to us this time and release the young man. You will be treated as a virus, and we are the cure,” concluded Anonymous in their statement. Several activist groups and human rights groups including Amnesty International have claimed that Nimr was not granted the means to a lawyer and that he was forced into signing a “confession” after suffering torture by prison officers. At the time, a Saudi court judgement read: [Nimr] encouraged pro-democracy protests [using] a Blackberry. Amnesty International recently released a report that proclaims Saudi Arabia as “one of the most prolific executioners in the world.” Between January 1986 and June 2015, at least 2,200 known people were executed, half of whom were foreign nationals. Executions were carried out for “crimes” such as witchcraft, sorcery and adultery. According to news reports, Saudi Arabia will imminently behead and then crucify Al Nimr, now 20, today or later this week. Source: https://hacked.com/anonymous-attacks-several-saudi-arabian-websites-brings-focus-teens-execution-opnimr/
More:
Anonymous Launches DDoS Attacks Several Saudi Arabian Websites, Brings Focus to a Teen’s Execution #OpNimr

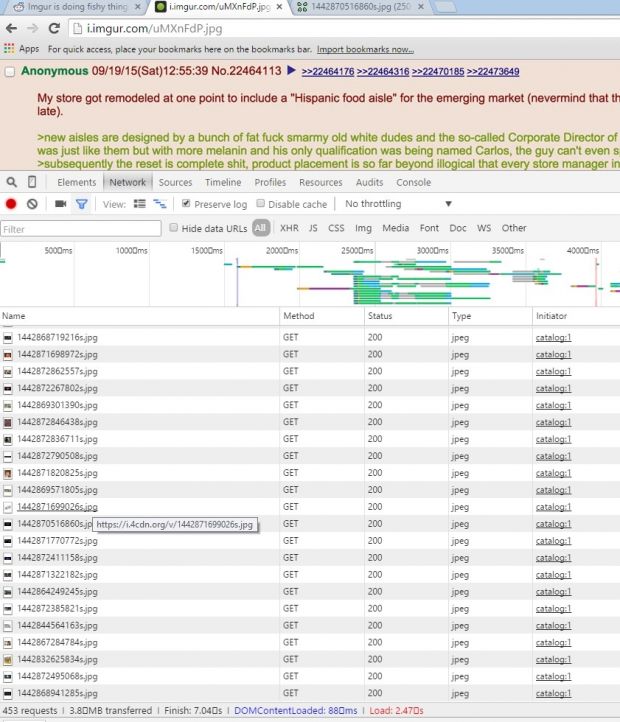
 A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml
A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml