Most DDoS defence solutions are missing critical parts of the threat landscape thanks to a lack of proper visibility. Online organisations need to take a closer look at the problem of business disruption resulting from the external DDoS attacks that every organisation is unavoidably exposed to when they connect to an unsecured or ‘raw’ Internet feed. Key components of any realistic DDoS defense strategy are proper visualisation and analytics into these security events. DDoS event data allows security teams to see all threat vectors associated with an attack – even complex hybrid attacks that are well disguised in order to achieve the goal of data exfiltration. Unfortunately, many legacy DDoS defense solutions are not focused on providing visibility into all layers of an attack and are strictly tasked with looking for flow peaks on the network. If all you are looking for is anomalous bandwidth spikes, you may be missing critical attack vectors that are seriously compromising your business. In the face of this new cyber-risk, traditional approaches to network security are proving ineffective. The increase in available Internet bandwidth, widespread access to cyber-attack software tools and ‘dark web’ services for hire, has led to a rapid evolution of increasingly sophisticated DDoS techniques used by cyber criminals to disrupt and exploit businesses around the world. DDoS as a diversionary tactic Today, DDoS attack techniques are more commonly employed by attackers to do far more than deny service. Attack attempts experienced by Corero’s protected customers in Q4 2014 indicate that short bursts of sub-saturating DDoS attacks are becoming more of the norm. The recent DDoS Trends and Analysis report indicates that 66% of attack attempts targeting Corero customers were less than 1Gbps in peak bandwidth utilisation, and were under five minutes in duration. Clearly this level of attack is not a threat to disrupt service for the majority of online entities. And yet the majority of attacks utilising well known DDoS attack vectors fit this profile. So why would a DDoS attack be designed to maintain service availability if ‘Denial of Service’ is the true intent? What’s the point if you aren’t aiming to take an entire IT infrastructure down, or wipe out hosted customers with bogus traffic, or flood service provider environments with massive amounts of malicious traffic? Unfortunately, the answer is quite alarming. For organisations that don’t take advantage of in-line DDoS protection positioned at the network edge, these partial link saturation attacks that occur in bursts of short duration, enter the network unimpeded and begin overwhelming traditional security infrastructure. In turn, this activity stimulates un-necessary logging of DDoS event data, which may prevent the logging of more important security events and sends the layers of the security infrastructure into a reboot or fall back mode. These attacks are sophisticated enough to leave just enough bandwidth available for other multi-vector attacks to make their way into the network and past weakened network security layers undetected. There would be little to no trace of these additional attack vectors infiltrating the compromised network, as the initial DDoS had done its job—distract all security resources from performing their intended functions. Multi-vector and adaptive DDoS attack techniques are becoming more common Many equate DDoS with one type of attack vector – volumetric. It is not surprising, as these high bandwidth-consuming attacks are easier to identify, and defend against with on-premises or cloud based anti-DDoS solutions, or a combination of both. The attack attempts against Corero’s customers in Q4 2014 not only employed brute force multi-vector DDoS attacks, but there was an emerging trend where attackers have implemented more adaptive multi-vector methods to profile the nature of the target network’s security defenses, and subsequently selected a second or third attack designed to circumvent an organisation’s layered protection strategy. While volumetric attacks remain the most common DDoS attack type targeting Corero customers, combination or adaptive attacks are emerging as a new threat vector. Empowering security teams with DDoS visibility As the DDoS threat landscape evolves, so does the role of the security team tasked with protecting against these sophisticated and adaptive attacks. Obtaining clear visibility into the attacks lurking on the network is rapidly becoming a priority for network security professionals. The Internet connected business is now realising the importance of security tools that offer comprehensive visibility from a single analysis console or ‘single pane of glass’ to gain a complete understanding of the DDoS attacks and cyber threats targeting their Internet-facing services. Dashboards of actionable security intelligence can expose volumetric DDoS attack activity, such as reflection, amplification, and flooding attacks. Additionally, insight into targeted resource exhaustion attacks, low and slow attacks, victim servers, ports, and services as well as malicious IP addresses and botnets is mandatory. Unfortunately, most attacks of these types typically slide under the radar in DDoS scrubbing lane solutions, or go completely undetected by cloud based DDoS protection services, which rely on coarse sampling of the network perimeter. Extracting meaningful information from volumes of raw security events has been a virtual impossibility for all but the largest enterprises with dedicated security analysts. Next generation DDoS defense solutions can provide this capability in a turn-key fashion to organisations of all sizes. By combining high-performance in-line DDoS event detection and mitigation capabilities with sophisticated event data analysis in a state-of-the-art big data platform, these solutions can quickly find the needles in the haystack of security events. With the ability to uncover hidden patterns of data, identify emerging vulnerabilities within the massive streams of DDoS attack and security event data, and respond decisively with countermeasures, next-generation DDoS first line of defense solutions provide security teams with the tools required to better protect their organization against the dynamic DDoS threat landscape. Source: http://www.information-age.com/technology/security/123459482/how-organisations-can-eliminate-ddos-attack-blind-spot
Read this article:
How organisations can eliminate the DDoS attack ‘blind spot’

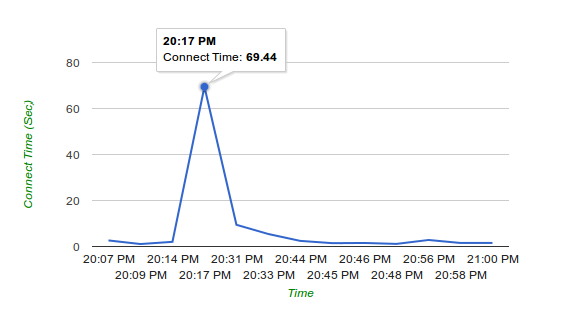
 The admin of Therealdeal market ( http://trdealmgn4uvm42g.onion/ ) provided us with some insights about the recent DDo’s attacks that are hitting all the major DNM’s in the past week: In the past few days, it seems like almost every DN market is being hit by DDoS attacks. Our logs show huge amounts of basic http requests aiming for dynamic pages, probably in attempt to (ab)use as many resources as possible on the server side, for example by requesting for pages that execute many sql queries or generate captcha codes. As we are security oriented we manged to halt the attack on our servers the moment it showed up in the logs. Although this required fast thinking, due to the fact that dealing with this kind of attack over tor is not the same as dealing with such attack over clearnet. New addresses? Shifting Pages? Waiting? All these did not work for other markets… Here you can see the beginning and failure, as caught by Dnstats: As you can see, our market’s response time spiked to almost 70 seconds while our market’s usual response time is insanely fast, almost like most clearnet sites. But also, you can see that the response time was back to 2-3 seconds a little after. Here is an example of a darknet market that didn’t know how to combat this problem: The flat line at 0 seconds meaning there was no response from the server. The Problem As opposed to cleanet attacks, where mitigation steps could be taken by simply blocking the offending IP addresses,when it comes to tor, the requests are coming from the localhost (127.0.0.1) IP address as everything is tunneled through tor. Another problem is the fact that the attackers are using the same user-agent of tor browser – hence we cannot drop packets based on UA strings. The attackers are also aiming for critical pages of our site – for example the captcha generation page. Removing this page will not allow our users to login, or will open the site to bruteforce attempts. Renaming this page just made them aim for the new url (almost instantly, seems very much automated). One of the temporary solutions was to run a script that constantly renamed and re-wrote the login page after 1 successful request for a captcha… Attacks then turned into POST requests aiming for the login page. Solutions If you are a DNM owner or just the security admin, check your webserver logs. There is something unique in the HTTP requests, maybe a string asking you to pay to a specific address. (assuming these are the same offenders). Otherwise there might be something else … Hint: you might need to load tcpdump during an attack. Hopefully, you are not using some kind of VPS and have your own dedicated servers and proxy servers. Or if you are using some shit VPS, then hopefully you are using KVM or XEN. (first reason being the memory is leakable and accessible by any other user of the same service). The other reason is – control on the kernel level. You can drop packets containing specific strings by using iptables, or use regex too. This is one example of a commad that we executed (amongst others) to get rid of the offenders, we cannot specify all of them, so be creative! iptables -A INPUT -p tcp –dport 80 -m string –algo bm –string “(RANSOM_BITCOIN_ADDRESS)” -j DROP Where (RANSOM_BITCOIN_ADDRESS) is the unique part of the request… To Other Market Admins: There are additional things to be done, but if we expose them, this will only start a cat and mouse game with these attackers. If you are a DNM admin feel free to sign up as a buyer at TheRealDeal Market and send us a message (including your commonly used PGP), since at the end of the day even though you might see us a competitor in a way, there are some things (like people stuck without their pain medication from mexico) that are priceless… Source: http://www.deepdotweb.com/2015/05/11/this-is-the-ransom-ddos-that-is-hitting-the-dark-net-markets/
The admin of Therealdeal market ( http://trdealmgn4uvm42g.onion/ ) provided us with some insights about the recent DDo’s attacks that are hitting all the major DNM’s in the past week: In the past few days, it seems like almost every DN market is being hit by DDoS attacks. Our logs show huge amounts of basic http requests aiming for dynamic pages, probably in attempt to (ab)use as many resources as possible on the server side, for example by requesting for pages that execute many sql queries or generate captcha codes. As we are security oriented we manged to halt the attack on our servers the moment it showed up in the logs. Although this required fast thinking, due to the fact that dealing with this kind of attack over tor is not the same as dealing with such attack over clearnet. New addresses? Shifting Pages? Waiting? All these did not work for other markets… Here you can see the beginning and failure, as caught by Dnstats: As you can see, our market’s response time spiked to almost 70 seconds while our market’s usual response time is insanely fast, almost like most clearnet sites. But also, you can see that the response time was back to 2-3 seconds a little after. Here is an example of a darknet market that didn’t know how to combat this problem: The flat line at 0 seconds meaning there was no response from the server. The Problem As opposed to cleanet attacks, where mitigation steps could be taken by simply blocking the offending IP addresses,when it comes to tor, the requests are coming from the localhost (127.0.0.1) IP address as everything is tunneled through tor. Another problem is the fact that the attackers are using the same user-agent of tor browser – hence we cannot drop packets based on UA strings. The attackers are also aiming for critical pages of our site – for example the captcha generation page. Removing this page will not allow our users to login, or will open the site to bruteforce attempts. Renaming this page just made them aim for the new url (almost instantly, seems very much automated). One of the temporary solutions was to run a script that constantly renamed and re-wrote the login page after 1 successful request for a captcha… Attacks then turned into POST requests aiming for the login page. Solutions If you are a DNM owner or just the security admin, check your webserver logs. There is something unique in the HTTP requests, maybe a string asking you to pay to a specific address. (assuming these are the same offenders). Otherwise there might be something else … Hint: you might need to load tcpdump during an attack. Hopefully, you are not using some kind of VPS and have your own dedicated servers and proxy servers. Or if you are using some shit VPS, then hopefully you are using KVM or XEN. (first reason being the memory is leakable and accessible by any other user of the same service). The other reason is – control on the kernel level. You can drop packets containing specific strings by using iptables, or use regex too. This is one example of a commad that we executed (amongst others) to get rid of the offenders, we cannot specify all of them, so be creative! iptables -A INPUT -p tcp –dport 80 -m string –algo bm –string “(RANSOM_BITCOIN_ADDRESS)” -j DROP Where (RANSOM_BITCOIN_ADDRESS) is the unique part of the request… To Other Market Admins: There are additional things to be done, but if we expose them, this will only start a cat and mouse game with these attackers. If you are a DNM admin feel free to sign up as a buyer at TheRealDeal Market and send us a message (including your commonly used PGP), since at the end of the day even though you might see us a competitor in a way, there are some things (like people stuck without their pain medication from mexico) that are priceless… Source: http://www.deepdotweb.com/2015/05/11/this-is-the-ransom-ddos-that-is-hitting-the-dark-net-markets/