VANCOUVER , April 8, 2015 /PRNewswire/ – DOSarrest Internet Security, a fully managed cloud based DDoS protection service, today announced that their DOSarrest External Monitoring Service (DEMS), a real-time website monitoring tool, launches a new iOS and Android application for clients. This application is a complimentary service to all DOSarrest clients who are subscribed to DOSarrest’s industry leading DDoS protection service. The new mobile application on iOS and Android will allow clients to easily access and view their website(s) status and performance in real-time 24/7/365, as well as enable them to historically view all of the statistics for up to 1 year from 8 globally distributed sensors. Jag Bains, CTO of DOSarrest says “This application is beneficial to all of our clients who have a mission critical website that requires 100% uptime. Unlike other monitoring services, this service is fully managed 24/7/365. Should anything unexpected occur, our engineers will investigate, pinpoint and advise the client on a solution in near real-time. No other vendor in this industry offers this level of customer service.” “We have a number of clients who depend on this service and some have subscribed to it that aren’t even using our DDoS protection service,” says Mark Teolis , CEO of DOSarrest. “With the new mobile application, in one click on your smart phone, you can view what sites are up or down and why in real-time, whenever and wherever you are. It’s like the laptop version in your pocket.” Teolis adds “As I far as I know, no other DDoS protection service or CDN offers any such complimentary service that compares to our External Monitoring Service, with 8 globally distributed sensors completely independent of any of our scrubbing nodes.” About DOSarrest Internet Security: DOSarrest founded in 2007 in Vancouver, B.C. , Canada , is one of only a couple of companies worldwide to specialize in cloud based DDoS protection services . Additional Web security services offered are Cloud based W eb A pplication F irewall (WAF), V ulnerability T esting and O ptimization (VTO) as well as cloud based global load balancing. SOURCE: http://www.prnewswire.com/news-releases/dosarrest-external-monitoring-service-launches-ios-and-android-app-499026641.html
Read More:
DOSarrest External Monitoring Service launches iOS and Android App

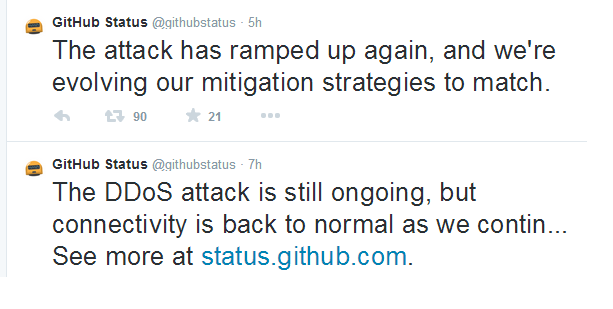
 San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/
San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/