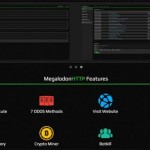
 Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml
Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml
Link:
Author of MegalodonHTTP DDoS Malware Arrested in Norway

