The attack also reached 110 million packets per second On June 14, a Chinese gambling company was unlucky enough to be at the end of a complex multi-vector DDoS attack that blasted over 470 gigabits per second (Gbps) and over 110 million packets per second (Mpps) at its servers. The attack came after the company had already faced multiple 250+ Gbps attacks in the previous days. The good news is that this 470 Gbps attack only lasted four hours and was deflected by the company’s DDoS mitigation service. Nine-vector DDoS attacks are rare Even if short, the attack itself was extremely complex, with the crooks utilizing nine different attack vectors. Compared to data from the first quarter of 2016, nine-vector DDoS attacks are extremely rare and happen once every 500 attacks (0.2% of all attacks). This particular attack started with a basic network-level assault that wanted to suffocate the network with large amounts of data. It first blasted SYN payloads, then generic TCP and UDP data packets. From the get-go, the attack was different from all the previous attacks, throwing over 300 Gbps at its target from its initial seconds, before growing bigger to reach its peak value. Attack evolved from network to application level Midway through the attack, the crooks completely changed tactics. They stopped the network-level attack and shifted to an application layer DDoS, during which attackers send packets of a smaller size, but in larger numbers to occupy the memory of the receiving servers. Incapsula, the company that was providing DDoS mitigation, said that in Q1 2016, it regularly mitigated application layer 50+ Mpps DDoS attacks every four days, and 80+ Mpps attacks every eight days. Even if this attack exceeded 110 Mpps, the company was able to mitigate the threat. The combination of all these vectors makes this one of the most complex attacks the company saw. In fact, Incapsula said this was the biggest DDoS attack it mitigated in terms of sheer size (470 Gbps) in its entire history. “On a technical level we want to make clear that there isn’t much difference in mitigating 300, 400, or 500 Gbps network layer attacks,” Incapsula’s Igal Zeifman and Ofer Gayer explain. “They’re similar threats, each dealt with in a similar manner. Large attack waves aren’t more dangerous than smaller ones. All you need is a bigger boat.” Source: http://news.softpedia.com/news/chinese-gambling-company-was-target-of-a-nine-vector-470-gbps-ddos-attack-505850.shtml#ixzz4D57R4eWd
Read More:
Chinese Gambling Company Was Target of a Nine-Vector 470 Gbps DDoS Attack


 While most of Lizard Squad’s first members are in jail or hiding and hoping that law enforcement won’t come knocking on their door, the group continues to live on through new members, new attacks, but also through the LizardStresser toolkit, which they leaked online at the start of 2015. The toolkit was heavily forked and adapted, as many other hacking groups sought to use it to create their own botnets to use for DDoS attacks, either just to annoy people, extort companies or hacktivism activities. LizardStresser is geared towards infecting IoT devices Arbor Networks says that LizardStresser is not extremely complicated, and is nothing more than a DDoS attack toolkit that uses the ancient IRC protocol to communicate between the C&C server and the client-side component. Because LizardStresser is coded in C and designed to run on Linux architectures, Arbor Networks says that a lot of groups that are deploying new LizardStresser instances are taking advantage of unsecured IoT devices running on platforms such as x86, ARM, and MIPS, where a stripped-down Linux version is the preferred OS. We touched on this topic last year when Lizard Squad’s new members were having trouble with their own botnet after unknown security researchers were trying to hijack some of these infected IoT systems. Webcams make the bulk of the LizardStresser-based botnets According to Arbor Networks, most of these infected IoT devices are Internet-connected webcams, accessible through a page broadcasting the “NETSurveillance WEB” title, and using their default access passwords. In a DDoS attack of over 400 Gbps aimed at a gaming site, Arbor says that 90% of the bots that participated in the attack were these type of webcams. The DDoS attacks are extremely simple and don’t even use traffic amplification/reflection techniques. LizardStresser was created to launch direct DDoS attacks, meaning the bots send UDP or TCP floods directly to the target. LizardStresser launches direct DDoS attacks, no protocol amplification Because of the massive amount of unsecured IoT devices, groups that use LizardStresser can launch massive DDoS attacks, previously thought to be unachievable without UDP-based amplification protocols such as NTP or SNMP. Furthermore, LizardStresser also includes a telnet brute-forcing feature that’s used to test new devices for default passwords and inform the C&C server about possible new victims. All of these make features make LizardStresser a popular choice when hacking outfits and hacktivism groups are looking for tools to build or broaden their DDoS capabilities. Overall, there’s a growing trend in terms of hacking groups adopting LizardStresser. “LizardStresser is becoming the botnet-du-jour for IOT devices given how easy it is for threat actors to make minor tweaks to telnet scanning,” says Matthew Bing of Arbor Networks. “With minimal reseach [sic] into IOT device default passwords, they are able to enlist an exclusive group of victims into their botnets.” Number of C&C servers using LizardStresser in 2016 Source: http://news.softpedia.com/news/there-are-over-100-ddos-botnets-based-on-lizard-squad-s-lizardstresser-505816.shtml#ixzz4D0b6wPkw
While most of Lizard Squad’s first members are in jail or hiding and hoping that law enforcement won’t come knocking on their door, the group continues to live on through new members, new attacks, but also through the LizardStresser toolkit, which they leaked online at the start of 2015. The toolkit was heavily forked and adapted, as many other hacking groups sought to use it to create their own botnets to use for DDoS attacks, either just to annoy people, extort companies or hacktivism activities. LizardStresser is geared towards infecting IoT devices Arbor Networks says that LizardStresser is not extremely complicated, and is nothing more than a DDoS attack toolkit that uses the ancient IRC protocol to communicate between the C&C server and the client-side component. Because LizardStresser is coded in C and designed to run on Linux architectures, Arbor Networks says that a lot of groups that are deploying new LizardStresser instances are taking advantage of unsecured IoT devices running on platforms such as x86, ARM, and MIPS, where a stripped-down Linux version is the preferred OS. We touched on this topic last year when Lizard Squad’s new members were having trouble with their own botnet after unknown security researchers were trying to hijack some of these infected IoT systems. Webcams make the bulk of the LizardStresser-based botnets According to Arbor Networks, most of these infected IoT devices are Internet-connected webcams, accessible through a page broadcasting the “NETSurveillance WEB” title, and using their default access passwords. In a DDoS attack of over 400 Gbps aimed at a gaming site, Arbor says that 90% of the bots that participated in the attack were these type of webcams. The DDoS attacks are extremely simple and don’t even use traffic amplification/reflection techniques. LizardStresser was created to launch direct DDoS attacks, meaning the bots send UDP or TCP floods directly to the target. LizardStresser launches direct DDoS attacks, no protocol amplification Because of the massive amount of unsecured IoT devices, groups that use LizardStresser can launch massive DDoS attacks, previously thought to be unachievable without UDP-based amplification protocols such as NTP or SNMP. Furthermore, LizardStresser also includes a telnet brute-forcing feature that’s used to test new devices for default passwords and inform the C&C server about possible new victims. All of these make features make LizardStresser a popular choice when hacking outfits and hacktivism groups are looking for tools to build or broaden their DDoS capabilities. Overall, there’s a growing trend in terms of hacking groups adopting LizardStresser. “LizardStresser is becoming the botnet-du-jour for IOT devices given how easy it is for threat actors to make minor tweaks to telnet scanning,” says Matthew Bing of Arbor Networks. “With minimal reseach [sic] into IOT device default passwords, they are able to enlist an exclusive group of victims into their botnets.” Number of C&C servers using LizardStresser in 2016 Source: http://news.softpedia.com/news/there-are-over-100-ddos-botnets-based-on-lizard-squad-s-lizardstresser-505816.shtml#ixzz4D0b6wPkw 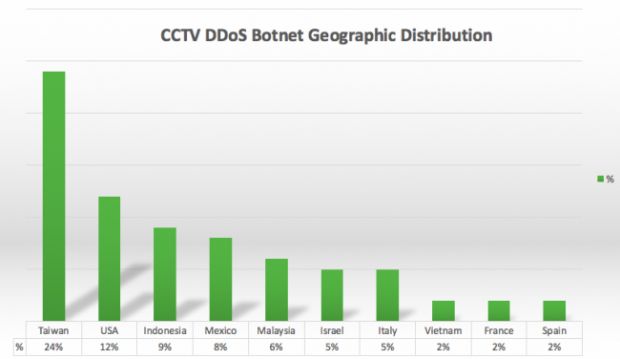
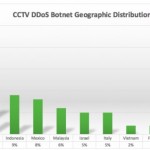 All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A
All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A