The popular website Tux Machines has evidently fallen victim to a DDoS attack that made the site unavailable for part of the day on Friday. The announcement of the attack was initially made in a blog notice posted on the site late Friday morning GMT which opened with the line “Tux Machines has been mostly offline this morning.” According to the blog post, the attack was at first thought to have been initiated by the Chinese web services company Baidu, but a later update indicated that turned out not to be the case. “…Baidu was [not] at fault but botmasters who used ‘Baidu’ to masquerade themselves, hiding among some real and legitimate requests from Baidu (with Baidu-owned IP addresses).” At this time, it’s not known who’s behind the attack. Roy Schestowitz, who with his wife Rianne publishes both Tux Machines and the politically oriented FOSS blog site Techrights, told FOSS Force, “We’ve suspected EPO seeking revenge, which makes sense for Techrights, not Tux Machines.” EPO refers to the European Patent Office which recently threatened Schestowitz with civil action over an article which claimed the EPO purposefully gives priority to patent applications from large corporations. This isn’t the first time the outspoken Schestowitz’s sites have come under DDoS attacks. In September and October of 2014, both sites came under a crippling attack that lasted for several weeks and which left both sites unreachable for long stretches of time. Indications are that this current attack isn’t nearly as damaging, although Schestowitz said that he and his wife had been working to keep Tux Machines functional throughout the weekend. Many websites use the services of a content delivery network (CDN), in part as protection against all but the most robust DDOS attacks. Schestowitz told us that no CDN is used by either of his sites. “I wrote a lot about this before,” he said. “Performance, Tor, privacy issues, JavaScript and so on. So no, CDNs are out of the question.” We sent Tux Machines an email this morning to determine the current status but have not received a reply. However, at the time of publication the site was responsive, as was Techrights. Source: http://fossforce.com/2015/11/tux-machines-again-face-ddos-attacks/
Monthly Archives: November 2015
Netherlands public broadcaster hit in worst-ever DDoS attack
The Netherlands public broadcaster NPO was hit by the largest DDoS attack ever, leaving the NOS site and app unreachable for some time on Sunday night. Other national and regional broadcasters’ sites were still online, but difficult to reach. During a DDoS attack a computer system is bombarded with an extreme number of visits. “We are used to large groups of users with big news, but this number surpassed everything. And all at the same time”, NPO said, according to NOS. The public broadcaster is considering which measures to implement, on top of the measures already in place, to prevent similar disturbances in future. The perpetrators behind the attack have not yet been identified. Source: http://www.nltimes.nl/2015/11/30/netherlands-public-broadcaster-hit-in-worst-ever-ddos-attack/
Read More:
Netherlands public broadcaster hit in worst-ever DDoS attack
It’s Black Friday: Do you know who is DDoSing your servers? And how to stop them
Today is Black Friday in the U.S. a retail holiday where numerous, extravagant deals are revealed to a ravenous public. In the brick and mortar universe, this can become a free-for-all when shoppers will camp out for days in front of a store just to get in on the first deals. In the cyber universe the same greatly increase traffic can be seen and this also makes it hunting season for hackers and extortionists attempting to get a cut. On the Internet, the easiest and lowest form of disruption is the distributed denial of service (DDoS) attack and we’ve seen it employed throughout the year by for various reasons to take down websites. To get a better understanding of what e-retailers can expect now on Black Friday and the upcoming Cyber Monday, SiliconANGLE reached out to Nexusguard (Nexusguard Limited), DDoS protection experts, and spoke with their Chief Scientist Terrence Gareau. “Risk from cyberattack is a trend repeating every year,” says Gareau. “No doubt retailers all experience an uptick in attacks [during Black Friday]. Attackers are definitely taking advantage of the uptick and e-tailers need to put in more resources to boost their websites’ security.” This year DDoS attacks hit record highs, according to the State of the Internet report from Akamai for Q2 2015. The number of attacks grew by 132 percent compared to the same time in 2014 and 12 attacks occurred that exceeded 1,000 gigabits per second (Gbps). Nexusguard’s own overwatch on DDoS showed that during 2015 Q3 attack numbers rose by 53 percent over Q2, higher than any quarter over the past two years. E-commerce at more risk than ever from DDoS attacks Most DDoS attacks that make it to the news are being done my Internet mayhem groups looking for fame and attention. The most recent example is the attack committed by Lizard Squad on Christmas Day, December 26, 2014 against the Xbox LIVE and PlayStation networks that knocked the gaming services offline for millions of customers However, Gareau says that not all DDoS attacks come from people seeking attention—some are seeded with greed and extortion. Especially when it comes to the lesser-known attacks that services and e-retailers suffer around this time of year. When asked if competitors might use DDoS to knock out or weaken sales from other e-retailers, Nexusguard’s chief scientist would only say that it does appear that competitors do attack each other this time of year. That said, more danger appears to be coming from extortion rackets this time of year than from greedy competitors. The usual strategy is to hit an outlet with a DDoS attack (a short one) and then send an e-mail requesting some sort of ransom payment or the attack comes back. A few more blasts might come along to get the target’s attention. “Hackers are aware that the holidays are a prime time for online retailers. Therefore, they would do anything to break through any defenses,” says Gareau. This time of year criminals know that stores and e-retailers are looking to make as much money as possible off traffic. As well, increased traffic makes servers even more vulnerable to DDoS because it means they’re already working at capacity. Attackers see this as low-hanging fruit because first it’s easier and second an e-retailer will lose a great deal of money for even ten minutes of time offline during the sales rush. “One of the most sophisticated attacks focused on the login prompt,” Gareau adds, when asked for an example of how hackers attempt to knock sites offline. “In fact, on Thanksgiving and Christmas last year, we saw a hacker craft specific requests to the login form, preventing visitors from logging on.” Cold advice about DDoS extortion: “…don’t f**ing pay ‘em.” “We expect to see an increase in fraud and extortion, directly linked to DDoS as seen over the last few years,” Gareau says. When it comes to handling the potential of (or ongoing) DDoS attacks, Gareau suggests getting a proper team on board, he works for such a team at Nexusguard after all, but he also has an opinion on extortion and it’s a very simple one: “…And don’t f**ing pay ‘em,” he adds. This year has a perfect example of why paying DDoS extortion is a losing bet. In early November Switzerland-based ProtonMail, a provider of end-to-end encrypted e-mail, was struck by a powerful DDoS attack and the attackers demanded a ransom of $6,000 to relent. (The amount requested was 15 bitcoins, which at the time came out to approximately $5,850.) ProtonMail paid the ransom but then paid the price: the ProtonMail website and service were washed away by a DDoS attack anyway. Paying extortion to make a DDoS attacker go away does not necessarily make them go away. Just like any other criminal enterprise, knowing that a payment will come is a good way to make sure they will come back. Worse, it will fund the criminals to build out or increase their total power, which means they can go after other targets more frequently. In many cases that ransom requested by the criminals behind the DDoS could be paid to an anti-DDoS outfit and used to lessen the impact of the attack. The result is that the criminals get nothing but time wasted firing off their attack tools. Source: http://siliconangle.com/blog/2015/11/27/its-black-friday-do-you-know-who-is-ddosing-your-servers-and-how-to-stop-them/
Read more here:
It’s Black Friday: Do you know who is DDoSing your servers? And how to stop them
Finance, telco and IT sectors were top targets for DDoS attacks in 2015
A new study conducted by Kasperky Labs and B2B International, has revealed that around one in four IT, telecommunication, and financial services companies have experienced a distributed denial of service (DDoS) attack over the last year. Almost half of the financial businesses understand that they are a prime target for these attacks while IT and telecommunication companies do not believe they are as at risk. This is dangerous because it could leave them more vulnerable to potential attacks. DDoS attacks have grown in popularity amongst cyber criminals and have been used to extort money, disrupt a site’s operation, and serve as a distraction whilst another cyber attack is occurring. 75 per cent of businesses that were victims of DDoS attacks said that the timing of attacks corresponded with other security incidents. Evgeny Vigovsky, Head of Kaspersky DDoS Protection, Kaspersky Lab said: “As the recent DDoS attacks on telecoms companies and banks reveal, businesses in these sectors represent prime targets for DDoS attackers. In some cases, DDoS attacks are a smokescreen for the cyber-theft or result in exorbitant ransom demands. That is why vulnerable sectors need to be extra-vigilant about security and be ready to deal with DDoS attacks. They need to build their understanding of the threat and choose the best protection against it. The days of DDoS attacks being an operational frustration that just resulted in some downtime are long over.” However the study showed that many companies are unaware of the threat of DDoS attacks and are unclear about how to stop them or contain them. Only 52 per cent of the companies surveyed felt that they had the necessary information regarding the intricacies of these attacks. This could be troublesome as DDoS attacks have become a popular tool among cyber criminals due to their difficulty to trace and ease to implement. Kaspersky Labs does offer DDoS protection to its customers and is able to reroute traffic allowing junk requests to be filtered out while legitimate traffic is forwarded to the site. This allows users to continue using the site or service safely even while an attack is taking place. Source: http://www.itproportal.com/2015/11/26/finance-telco-it-sectors-top-targets-for-ddos-attacks-2015/
View the original here:
Finance, telco and IT sectors were top targets for DDoS attacks in 2015
Anonymous vs ISIS, Australian attorney general, NTP and DDoS exploits
Anonymous vs ISIS Naturally, even cybersecurity news in this past week has centred around ISIS in the wake of the Paris attacks. The main headline has come from Anonymous, who have again but more formally waged ‘war’ on ISIS themselves. So far their efforts seem to have focused on communication; deleting thousands of Twitter accounts they believe are associated with the terrorist group. One notable aspect of how ISIS recruit supporters is through social media such as Twitter and Facebook, with an estimated 46,000 affiliated Twitter accounts. The move by Anonymous was announced immediately after ISIS dubbed the group ‘idiots’ and began circulating some useless cybersecurity advice to its followers via messaging app Telegram. Anonymous’s efforts, dubbed #OpParis are likely to irritate the group and possibly damage their recruitment opportunities. Australian attorney general warns terrorism means privacy will suffer Australian Attorney General George Brandis has said that Australians should expect ‘greater impediments to personal privacy’ in the wake of the Paris attacks. Measures have already become more strict under his tenure, with legislation passed to collect call records, IP addresses, location and billing information but it remains to be seen what further changes might be made. He also said during the interview by Nine Network that the situation with ISIS was tantamount to war. UK warns terrorists are targeting hospitals, power stations and air traffic control In an address at GCHQ (Government Communication Headquarters, a branch of British intelligence), chancellor George Osborne warned that terrorists will also be making efforts to target national infrastructure in order to carry out attacks. He also said that the government intend to double cybersecurity spending over the next five years. While we know such attacks are possible, we are yet to see terrorist groups like ISIS leverage this type of capability. NTP being made more secure to avoid DDoS exploits A new beta version of the Network Time Protocol (NTPsec) has been released, in efforts to avoid exploitation in DDoS attacks. Currently only available for open source use and feedback, the protocols codebase has been greatly streamlined; reduced from 30,000 lines of code to just 884. One of the project’s lead developers Eric S Raymond said: ‘The most important change you can’t see is that the code has been very seriously security-hardened, not only by plugging all publicly disclosed holes but by internal preventive measures to close off entire classes of vulnerabilities.’ Hackers offer 200,000 Comcast user passwords for sale Hackers have offered 200,000 Comcast user passwords for sale on the dark web, leading to a mass password reset from the company. What’s interesting in this case is that this was not a breach, but the result of users being duped into revealing their passwords themselves. Fortunately, Comcast’s own security officer discovered the passwords up for sale and initiated the mass reset before any accounts were known to be exploited. A reminder to be more careful with our password management! Vodafone reveal breach as further arrests made in TalkTalk case In the wake of the large TalkTalk breach and as a third man was arrested in the case, Vodafone announced their own breach. Affecting just 1827 users, who have all since been informed, Vodafone have not revealed how the attack was carried out. The number of customers affected by the TalkTalk breach has now been revised; originally given as 4 million, the number is now down to 1.2 million. In addition to usernames, emails and passwords 21,000 of these included bank account details and 28,000 credit card details. Source: https://www.acunetix.com/blog/articles/in-the-headlines-anonymous-vs-isis-australian-attorney-general-ntp-and-ddos-exploits/
Follow this link:
Anonymous vs ISIS, Australian attorney general, NTP and DDoS exploits

Bloggers Put Bounty on DDoS Extortionists
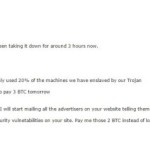 Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml
Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml
See the article here:
Bloggers Put Bounty on DDoS Extortionists
To the IT Security Rescue: DARPA and the Extreme DDoS Defence Program
IT security is a big deal – especially today with concerns that the government may be compromising some private networks. We know that the agency has compromised Google and Yahoo! in the past. Today, the Defence Advanced Research Projects Agency (DARPA) is working to fight against certain kinds of security breaches. On the surface of it, it seems contradictory, since DARPA is a branch of the U.S. Department of Defence. But, here’s a deeper look into the agency, and what they’re doing and why. DDoS Attacks and Why They’re Important A DDoS attack is a special type of DOS attack, commonly called a “Distributed Denial of Service” attack. It’s an attempt to bring down a network using multiple compromised systems, which are usually infected with malware or a virus – usually a trojan. The point of a denial of service attack is to make so many requests from the server that it can’t keep up, and crashes – taking the site or network offline. A distributed attack means that multiple computers are making requests for information or data from the server. And, because they are spread out, it’s very difficult to stop. It’s difficult to distinguish between legitimate users and attackers because, often, innocent computers are hijacked in the attack and made to look like legitimate users. Security companies that specialize in this type of threat know how to deal with them. And, you can visit this website if you want to know more about how detection and analysis works from inside the industry – including the concept of “white hat hacking” or “penetration testing.” Option One: Self-Defence Tactics One option commonly employed by companies and organizations in the past was a homebrew self-defence strategy. This is the simplest way to defend against an attack, but it’s also a method that’s a bit outdated. Usually, a coder or in-house IT employee would write some Python script that would filter out bad traffic. Sometimes, enterprises would use existing firewalls to block malicious traffic. In the early 2000s, this was a simple affair. Today, attacks are fairly complex and, while it’s simple to write a script, it doesn’t work nearly as well as it used to. A firewall will quickly be overloaded under the mildest of today’s DDoS attacks. Option Two: Specialized Equipment Defence Another option is to use specialized equipment to defend your company or organization. It’s a similar approach to the DIY method in that an enterprise is doing all of the work to stop an attack. However, instead of relying on scripts and firewalls, the business buys and deploys dedicated DDoS mitigation hardware. The hardware sits in a company’s data centre in front of the standard servers and routers. It’s made specifically to detect and filter malicious traffic. Companies that use this approach face multiple challenges. First, the hardware is costly. And, if the company isn’t under attack, the devices are just sitting there, collecting dust. They can also be expensive to operate. You need skilled network and security people to run them. They have to be constantly updated by your operations and IT team if you want protection against the latest threats. DDoS tactics change on a daily basis. And, finally, the Achilles heel of the hardware is that they can’t handle volumetric attacks. All an attacker has to do is figure out your maximum bandwidth and exceed it. Option Three: ISP Defence Most companies outsource their DDoS mitigation. Some enterprises use their ISP to provide the service. An ISP can have more bandwidth than a single company would, which helps with large attacks. But, there are still problems with this approach. The most obvious is that ISPs aren’t in the business of threat detection and mitigation. They sell bandwidth. So, their systems might not actually be very good at detecting and defending against a well-orchestrated (or even not-so-well orchestrated) attack. Option Four: Cloud Mitigation Provider This option essentially outsources the problem to a company that specializes in cloud services. Cloud mitigation providers are experts when it comes to providing DDoS mitigation from the cloud. In other words, these companies have built out massive network resources. They have more bandwidth capabilities than your average hosting provider or cloud storage vendor, and they can mitigate the threat of an attack at multiple sites around the Internet. Basically, they redistribute the bad traffic that comes in to lessen its effects. In many cases, there is no effect. They can scrub traffic for you, and send only the “clean” traffic to your data centre. One major reason you’d want to hire these people is for their expertise. They usually have network and security engineers and researchers on staff that are monitoring the latest threats and tactics hackers use so that customers are well-protected. They also have bandwidth – lots of it. They provide more bandwidth than an enterprise could ever hope to provision on its own. This is effective in stopping even the largest of attacks. They have multiple types of DDoS mitigation hardware. Since DDoS attacks are very complex, there’s an inherent need for multiple layers of filtering to keep up with the latest threats. Cloud providers use multiple technologies, including their own proprietary technology to defend against attacks. Source: http://www.theglobaldispatch.com/to-the-it-security-rescue-darpa-and-the-extreme-ddos-defence-program-68380/
More here:
To the IT Security Rescue: DARPA and the Extreme DDoS Defence Program
15-Year-Old Brit Charged with DDoS Attacks, Bomb Threats
British police have arrested and charged a 15-year-old teenager from Plympton, Plymouth. The boy was taken into custody at his parents’ house on Monday, November 16. According to police reports, the teen hacker launched several DDoS attacks from his home against companies and servers in Africa, Asia, Europe, and North America. Additionally, the hacker also made several bomb threats against North American airlines. He used social media to deliver his warnings. Because he’s a minor, the Devon & Cornwall Police did not reveal his name, but the youngster was freed on bail by his parents and will face a judge before Plymouth Youth Court on Friday, December 18. Official charges have been brought against the teenager under the Section 51 of the Criminal Law Act (two offenses for the bomb threats) and Section 3 of the Computer Misuse Act (three offenses for the DDoS attacks). Previously, UK police had arrested several teens in connection with the high-profile TalkTalk data breach . This is an unrelated case but still raises questions about the UK youth’s predilection to cyber-crime. With so many hacking tools available online, many teens find it extremely easy to launch large-scale attacks on “anyone who annoys them.” Things may have been made worse yesterday, when, in an attempt to increase attacks on ISIS members, the Anonymous hacktivism group published a noob’s guide to hacking . Source: http://news.softpedia.com/news/15-year-old-brit-charged-for-ddos-attacks-bomb-threats-496420.shtml
More:
15-Year-Old Brit Charged with DDoS Attacks, Bomb Threats
UK Broadband Provider AAISP Suffers Strong DDoS Assault
Internet provider Andrews and Arnold (AAISP) appears to have become the target for a semi-sporadic Distributed Denial of Service (DDoS) assault, which began hitting their network yesterday and has caused some of their customers to lose connection. Generally speaking DDoS attacks work by overloading a target server (e.g. a website or other network service) with masses of data requests from multiple internet connected computers / devices; usually Trojan/Virus infected computers that then become part of a botnet , which can be controlled by a single individual that usually hides their connection behind other servers. At this point it’s crucial to reflect that DDoS attacks happen to ISPs all the time (we read about them on an almost weekly basis), they’re practically par-for-the-course, but most can be mitigated and few are ever significant enough to knock lots of end-users offline. In nearly all cases these incidents aren’t actually an attack against the ISP, but rather somebody targeting a specific customer on the ISPs network. As such this should NOT be confused with the recent TalkTalk incident, which also involved a separate hacking attempt and was aimed at the ISPs web server. By comparison the assault against AAISP appears to have targeted part of their network and NOT their website, which is usually what happens when somebody is looking to knock a specific subscriber offline. The nature of this assault, which seems both powerful and aimed at several areas of their network, meant that AAISP’s “ usual anti-DOS systems have not helped “, although they were later able to “ mitigated most of the problems. ” Unfortunately the assault began again this morning and moved to a new target block, which has kept AAISP’s staff on their toes. Adrian Kennard, Director of AAISP, told ISPreview.co.uk: “ Staff have been working on this to reduce the impact on all customers as much as possible, and are continuing to do so today. There are still a handful customers that are collateral damage from the attack and we are working on getting those customers on line right now .” Apparently “ many ” of AAISPs customers have been affected by the DDoS, although only a handful were actually left without Internet connectivity and the provider is now attempting to identify which customers were being targeted by the assault (in practice they may not get to the bottom of this, just as most other ISPs rarely do). In the meantime some of provider’s customers are having their WAN IP address changed to get them on-line, including a few that own blocks of IPs (this can sometimes be a bit more tricky for the customer). One of those is Basingstoke based fixed wireless broadband ISP HiWiFi, which has been tweeting about the incident since last night. It’s worth pointing out that the Computer Misuse Act effectively makes DDoS illegal, although finding the perpetrators is rather more difficult, not least because such attacks are usually short-lived (the longer they go on the greater the chance of being traced and caught). Source: http://www.ispreview.co.uk/index.php/2015/11/uk-broadband-provider-aaisp-suffers-strong-ddos-assault.html
Continued here:
UK Broadband Provider AAISP Suffers Strong DDoS Assault
UK pummelled with DDoS after ISIS cyber attack warning
Earlier this week, the UK government warned ISIS militants were developing the capability to launch cyber attacks against Britain’s infrastructure. Today, we are witnessing a huge amount of DDoS (Distributed Denial of Service) attacks on the United Kingdom. As of writing, a look at the Digital Attack Map shows an unprecedented amount of attack traffic aiming towards the UK. Most of the DDoS attacks use “fragmentation” which sends a flood of TCP or UDP fragments to a victim, overwhelming the victim’s ability to re-assemble the streams and severely reducing performance. The cyber attacks come after a week of physical attacks towards the international community, and subsequent retaliation in the form of bombing campaigns against key IS targets in Syria and hundreds of raids on various safe houses being used to harbor the militants in France and Belgium. It’s unclear what the attack traffic is targeting, and whether it’s originating from IS sympathasisers, but online activist group Anonymous has been under attack for declaring war on the militants with the launch of their #OpParis campaign for anyone to disrupt social network accounts used for propaganda and recruitment by the group. An IRC used by Anonymous has temporarily had to shut-off external connections from third-party clients. #OpParis is not “hacking” in the traditional sense, as the group is often known for, in fact its rules prohibit carrying out certain attacks such as DDoS and instead focuses on using software to collect the social network accounts used by ISIS. Volunteers then use the services’ built-in tools for abuse reporting. So far, #OpParis has reportedly taken down 5,500 Twitter accounts – despite not all being confirmed as being ISIS-affiliated. ISIS has used the web for international recruitment, and for encrypted communications. The actions of Anonymous has worried the group as it’s disruptive to spreading their poisonous ideology to potential new recruits, but it has also pushed the militants into using safer messaging tools and issuing advice to followers over which services to use. The potential of using these encrypted services, like Telegram, for organising attacks out the view of intelligence agencies is concerning governments. David Cameron, Prime Minister of the United Kingdom, has expressed his government’s interest in “banning” encrypted messaging tools which agencies struggle to intercept. Cameron’s plan has been criticised not just for its privacy implications, but also for how it would be impossible to ban such tools in practice as most of the chosen tools are “open source” and can be distributed by anyone. In response to cyber attack threats, the UK government has pledged £2 billion towards creating a “National Cyber Centre” based at GCHQ (Government Communications Headquarters) Chancellor George Osborne said ISIS was trying to develop the capability to attack British infrastructure such as hospitals, power networks and air traffic control systems for lethal consequences. In a speech at GCHQ, he said “they have not been able to use it to kill people yet by attacking our infrastructure through cyber attack, but we know they want it and are doing their best to build it.” “We are building our own offensive cyber capability – a dedicated ability to counter-attack in cyberspace. When we talk about tackling (ISIS), that means tackling their cyber threat as well as their guns, bombs and knives,” he continued. It’s unclear if the cyber attacks towards the UK today are ISIS-related, but it goes to show the need for a facility dedicated towards facing cyber threats. Back in September, we reported about the creation of the Global Cyber Alliance. The alliance is headquartered in New York and London, but it’s unclear if this new investment will be an expansion of that scheme or an independent facility. Will Pelgrin, former CEO and President of the Center for Internet Security, said: “Cyber crimes have become a worldwide epidemic with estimates of a half billion global cyber victims annually. We must treat cyber security threats and crimes as we would any widespread infectious disease – immediately, urgently and collectively. Cyber risks have reached catastrophic proportions and, therefore, require an unparalleled, public/private and transnational response.” Source: http://www.telecomstechnews.com/news/2015/nov/18/uk-pummelled-ddos-after-isis-cyber-attack-warning/
Link:
UK pummelled with DDoS after ISIS cyber attack warning
