At the start of 2014, attackers’ favorite distributed denial of service attack strategy was to send messages to misconfigured servers with a spoofed return address – the servers would keep trying to reply to those messages, allowing the attackers to magnify the impact of their traffic. As those servers got patched, this strategy became less and less effective. But now it’s back, according to a new report from Akamai. Except this time, instead of hitting data center servers or DNS servers, the attackers are going after personal computers on misconfigured home networks. According to Eric Kobrin, Akamai’s director of information security responsible for adversarial resilience, the attackers are taking advantage of plug-and-play protocols, commonly used by printers and other peripheral devices. These attacks, known as Simple Service Discovery Protocol (SSDP) attacks, are now the single largest attack vector for DDoS attacks, accounting for 21 percent of all attacks, up from 15 percent last quarter, and less than 1 percent at this time last year. “There are infectable SSDP services all over the Internet,” he said. “As they are discovered, we help work with people to shut them down.” Although each particular device has just a fraction of the bandwidth available to data center-based servers, there are more of them. “There’s a fertile ground of home systems,” he said. “A property configured home firewall can block this, but there are many improperly configured home systems connected to the Internet – and there are also industrial systems that can be used to reflect attacks as well.” This attack source is also harder to shut down, he said. “It’s easier to go into the data center and have the service providers do the clean-up,” he said. Last quarter, SYN flood attacks – where “synchronize” messages are sent to servers – was the leading attack vector, accounting for 17 percent of all attacks, down slightly from 18 percent of all attacks at the start of 2014. There has also been a change in the size of the median attack, and the typical size range of attacks, Kobrin said, as defensive measures have improved. “The smallest effective attack size has increased, year over year,” he said. “It’s because the smallest attacks are no longer effective.” Another type of DoS attack has gained a foothold for the first time this year. SQL injections, normally used to gain access to systems for the purpose of stealing data, are now being used to shut down Web sites as well. Akamai saw more than 52 million SQL injection attacks during the first quarter of 2015, which accounted for 29 percent of all Web application attacks. The most common targets for SQL injection attacks were retail, travel and media websites. Finally, another attack vector that’s just now starting to make an impact is domain hijacking. “People are actually attacking the registries and getting their own information put in, so the big sites are losing control of their DNS infrastructure,” Korbin said. There have been a few high-profile cases so far, he said, mostly politically motivated, but not yet enough data to measure a trend. “We didn’t see it much in 2012, started seeing a little bit of it in 2013 and 2014, and seeing it more of it now,” he said. He recommended that companies switch on two-factor authentication for their email systems when available, ensure that employees don’t reuse credentials, ask their domain registrars to put a lock on their domains, and, finally, keep a close eye on traffic numbers to spot a drop-off as soon as it happens. With these domain redirects, the attackers are not only able to shut down the legitimate website, but also put up their own content under that website’s brand. Source: http://www.csoonline.com/article/2923832/business-continuity/ddos-reflection-attacks-are-back-and-this-time-its-personal.html
More:
DDoS reflection attacks are back


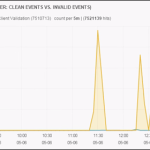 In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/
In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/