A team of Chinese academics has found a new way to abuse HTTP packets to amplify web traffic and bring down websites and content delivery networks (CDNs). Named RangeAmp, this new Denial-of-Service (DoS) technique exploits incorrect implementations of the HTTP “Range Requests” attribute. HTTP Range Requests are part of the HTTP standard and allow clients (usually browsers) to request only a specific portion (range) of a file from a server. The feature was created for pausing and resuming traffic in controlled (pause/resume actions) or uncontrolled (network congestion or disconnections) situations. The HTTP Range Requests standard has been under discussion at the Internet Engineering Task Force (IETF) for more than half a decade, but, due to its usefulness, has already been implemented by browsers, servers, and CDNs. Two RangeAmp attacks discovered Now, a team of Chinese academics says that attackers can use malformed HTTP Range Requests to amplify how web servers and CDN systems react when having to deal with a range request operation. The team says two different RangeAmp attacks exist. The first is called a RangeAmp Small Byte Range (SBR) attack. In this case [see (a) in the image below], the attacker sends a malformed HTTP range request to the CDN provider, which amplifies the traffic towards the destination server, eventually crashing the targeted site. The second is called a RangeAmp Overlapping Byte Ranges (OBR) attack. In this case [see b) in the image below], the attacker sends a malformed HTTP range request to a CDN provider, and in the case, the traffic is funneled through other CDN servers, the traffic is amplified inside the CDN networks, crashing CDN servers and rendering both the CDNs and many other destination sites inaccessible. Image: Weizhong et al. Academics said they tested RangeAmp attacks against 13 CDN providers and found that all were vulnerable to the RangeAmp SBR attack, and six were also vulnerable to the OBR variant when used in certain combinations. Researchers said the attacks were very dangerous and required a minimum of resources to carry out. Of the two, RangeAmp SBR attacks could amplify traffic the most. The research team found that attackers could use a RangeAmp SBR attack to inflate traffic from 724 to 43,330 times the original traffic. Image: Weizhong et al. RangeAmp OBR attacks were a little harder to carry out, as the six vulnerable CDNs needed to be in specific (master-surrogate) configurations, but when conditions were met, reserchers said OBR attacks could also be used to inflate traffic inside a CDN network with amplification factors of up to nearly 7,500 times the initial packet size. Image: Weizhong et al. Of the two, OBR attacks were considered more dangerous, as attackers could take down entire chunks of a CDN provider’s network, bringing down connectivity for thousands of websites at a time. CDN vendors notified seven months ago Academics said that for the past few months they have been silently contacting the affected CDN providers and disclosing the details of the RangeAmp attack. Of the 13 CDN providers, researchers said that 12 responded positively and either rolled out or said they planned to roll out updates to their HTTP Range Request implementation. The list includes Akamai, Alibaba Cloud, Azure, Cloudflare, CloudFront, CDNsun, CDN77, Fastly, G-Core Labs, Huawei Cloud, KeyCDN, and Tencent Cloud. “Unfortunately, although we have sent them emails several times and have tried to reach out to their customer services, StackPath did not provide any feedback,” the research team said. “In general, we have tried our best to responsibly report the vulnerabilities and provide mitigation solutions. The related CDN vendors have had nearly seven months to implement mitigation techniques before this paper was published.” Each CDN provider’s reply, along with technical details about the RangeAmp attacks, are available in the research team’s paper, entitled “CDN Backfired: Amplification Attacks Based on HTTP Range Requests,” available for download in PDF format from here. Source: https://www.zdnet.com/article/rangeamp-attacks-can-take-down-websites-and-cdn-servers/
See original article:
RangeAmp DDoS attacks can take down websites and CDN servers


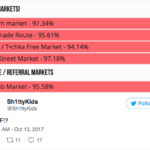 There seems to be some turbulence going on in the murky world of the dark web, with four of its major drug marketplaces unexpectedly going offline, reports said. The dark web is a section of the internet where people contact each other anonymously without the fear of being monitored. It is usually used by criminals to sell drugs, chemicals, weapons, child abuse images and even offer assassination services. Websites The Trade Route, Tochka, Wall Street Market and Dream Market, were down without any notification or clarification from the sites’ administrators. According to some users of such markets, this might either be a DDoS attack by a hacker or a large scale action by law enforcement authorities. However, there are more chances of the former happening than the latter. Some dark web users have also started complaining of botnet attacks. Another farfetched theory is that this is scam by a bunch of drug dealers — taking off with the money of their clients while not providing them with the required merchandize. With no notification or clarification from the sites’ administrators, the exact reason for the sudden disappearance of such marketplaces remains unclear. However, a user going by the name Automoderator commented on a the subreddit /r/DarkNetMarketNoobs that the WallStreetMarket is not listed currently, as it is facing “very serious issues” and warned others to avoid it all costs. Some other users on the subreddit say that the Dream Market has been working fine on all its mirrors, but, however its main site is down. At the time of writing, the marketplaces were still down, according to dark web marketplace tracker deepdotweb. Many sites on the dark web are also run by law enforcement — the Australian Police ran one of the world’s biggest child porn sites on the dark web between October 2016 and September 2017, called Child’s Play, in an effort to nab pedophiles. The police grabbed the administrator access from two cyber criminals — Benjamin Faulkner and Patrick Falte and started administering the sites. Police even posted more child porn on the site in an effort to convince the viewers that the site had not been taken over by the authorities. By the time they shut down the site, police were able to nab more than 90 pedophiles in Australia and 900 across the world. In case, the marketplaces were being taken over by law enforcement to nab drug traffickers and child porn purveyors, it might be a different case. However the development has many dark web users in a state of paranoia and many users have posted on Reddit reminding other users of such busts. Such attacks on dark web markets in the past have usually begun with large-scale DDoS attacks. In July, a massive trans-continental sting saw two of the dark web’s biggest sites at the time, AlphaBay and Hansa, being taken down. Law enforcement agencies claimed they were able to collect incriminating information on hundreds of buyers and vendors, going as far as threatening to prosecute them. Source: http://www.ibtimes.com/dark-web-marketplaces-go-down-reported-mass-ddos-attack-2601105
There seems to be some turbulence going on in the murky world of the dark web, with four of its major drug marketplaces unexpectedly going offline, reports said. The dark web is a section of the internet where people contact each other anonymously without the fear of being monitored. It is usually used by criminals to sell drugs, chemicals, weapons, child abuse images and even offer assassination services. Websites The Trade Route, Tochka, Wall Street Market and Dream Market, were down without any notification or clarification from the sites’ administrators. According to some users of such markets, this might either be a DDoS attack by a hacker or a large scale action by law enforcement authorities. However, there are more chances of the former happening than the latter. Some dark web users have also started complaining of botnet attacks. Another farfetched theory is that this is scam by a bunch of drug dealers — taking off with the money of their clients while not providing them with the required merchandize. With no notification or clarification from the sites’ administrators, the exact reason for the sudden disappearance of such marketplaces remains unclear. However, a user going by the name Automoderator commented on a the subreddit /r/DarkNetMarketNoobs that the WallStreetMarket is not listed currently, as it is facing “very serious issues” and warned others to avoid it all costs. Some other users on the subreddit say that the Dream Market has been working fine on all its mirrors, but, however its main site is down. At the time of writing, the marketplaces were still down, according to dark web marketplace tracker deepdotweb. Many sites on the dark web are also run by law enforcement — the Australian Police ran one of the world’s biggest child porn sites on the dark web between October 2016 and September 2017, called Child’s Play, in an effort to nab pedophiles. The police grabbed the administrator access from two cyber criminals — Benjamin Faulkner and Patrick Falte and started administering the sites. Police even posted more child porn on the site in an effort to convince the viewers that the site had not been taken over by the authorities. By the time they shut down the site, police were able to nab more than 90 pedophiles in Australia and 900 across the world. In case, the marketplaces were being taken over by law enforcement to nab drug traffickers and child porn purveyors, it might be a different case. However the development has many dark web users in a state of paranoia and many users have posted on Reddit reminding other users of such busts. Such attacks on dark web markets in the past have usually begun with large-scale DDoS attacks. In July, a massive trans-continental sting saw two of the dark web’s biggest sites at the time, AlphaBay and Hansa, being taken down. Law enforcement agencies claimed they were able to collect incriminating information on hundreds of buyers and vendors, going as far as threatening to prosecute them. Source: http://www.ibtimes.com/dark-web-marketplaces-go-down-reported-mass-ddos-attack-2601105