Just hours after Amazon announced a $970m deal to acquire Twitch, the live video platform for gamers was taken offline temporarily by a distributed denial of service (DDoS) attack. Twitch is the latest in a string of online gaming platforms to be hit by DDoS attacks that have been linked to several groups, including Lizzard Squad, jihadist group Islamic State, and Anonymous. At the weekend, Sony’s PlayStation Network was knocked offline and several others experienced disruptions, including Microsoft’s Xbox Live and Blizzard’s Battle.net. DDoS attacks are commonly used by competitors or activists to take services offline using a variety of techniques that make services impossible to reach. The reason for the DDoS attack on Twitch is unknown, but industry pundits have speculated that it may be linked to concerns about the acquisition by Amazon. Commenting on the weekend disruptions, Dave Larson, CTO at Corero Network Security, said the drivers for launching DDoS attacks are far ranging and difficult to pinpoint in many cases. “Anyone can become a victim at any time and, as the attacks continue to become stronger, longer and more sophisticated, businesses that rely on their online web applications as a revenue source cannot become complacent,” he said. Larson said the latest DDoS attacks underscore the importance of including a DDoS first line of defence as a component of network security architecture. Lancope chief technology officer TK Keanini said that while DDoS was once a resource held by a few of the elite groups on the net, this method of attack is now available to anyone as it is offered as a service. “If you know where to look, and you have some crypto currency in hand, just point and shoot,” he said. According to Keanini, any business connected to the internet is likely to be targeted by a DDoS attack at some point. “But game networks have to work harder than most to remain secure as they are incredibly attractive targets. “Not only are they high profile, with any disruption making the news, but given all the in-game commerce, credit card and personal information is kept up to date and can be monetised by these cyber criminals,” he said. Source: http://www.computerweekly.com/news/2240227573/DDoS-attack-downs-Twitch-on-news-of-Amazon-acquisition
See the original post:
DDoS attack downs Twitch on news of Amazon acquisition


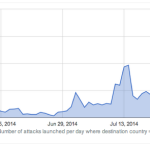 As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9
As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9