Pets make purrrfect pawns for surreptitious signal slurping A security boffin has created a ‘WarKitteh’ capable of sniffing WiFi packets.…
Continued here:
WiFi WarKitteh and DDoS Dog to stalk DEF CON 22

Pets make purrrfect pawns for surreptitious signal slurping A security boffin has created a ‘WarKitteh’ capable of sniffing WiFi packets.…
Continued here:
WiFi WarKitteh and DDoS Dog to stalk DEF CON 22
Cloudflare claims tip-off allowed it to tip traffic into sinkholes One of the largest and most sophisticated distributed denial of service (DDOS) attacks has hit a controversial online democracy poll canvassing opinion on future Hong Kong elections.…
See the article here:
‘Most sophisticated DDoS’ ever strikes Hong Kong democracy poll
Days after Feedly and Evernote were briefly forced offline by hackers demanding a ransom payment, a code-hosting service was run out of business by a similar scheme. CodeSpaces.com closed its doors this week, following a security breach that began with a distributed denial-of-service (DDoS) attack, and ended 12 hours later after an attempt to extort money from the company. No stranger to DDoS attacks, Code Spaces thought it could handle the situation, but the situation quickly spiraled out of control. On Tuesday, an unauthorized person—not believed to be employed by the site—gained access to Code Spaces’s Amazon EC2 control panel. When the team fought back, the hacker deleted “most of our data, backups, machine configurations and offsite backups,” the company said. “Code Spaces will not be able to operate beyond this point,” an online notice said, citing the price of resolving the issue, as well as the expected cost of refunding paying customers. This week’s attack “will put Code Spaces in [an] irreversible position both financially and in terms of ongoing credibility.” “All that we have to say at this point is how sorry we are to both customers and to the people who make a living at Code Spaces for the chain of events that lead us here,” the company said. Users can expect more details once Code Spaces sorts out its customers’ needs. Those who have stored data on the site can email support@codespaces.com with an account URL, and if you’re lucky, some remaining crumbs will be returned. For more, watch PCMag Live in the video below, which the Code Spaces dilemma. It’s been a banner month for DDoS attacks: Evernote suffered a blow last week, but was back on its feet within a few hours. Feedly wasn’t so lucky, however. The RSS service was hit twice in two days, though the company promised user data remained safe. Similarly, Ancestry.com just recovered today from a three-day bout of DDoS, in which the site was overloaded with traffic and crashed. No user information was compromised. Source: http://www.pcmag.com/article2/0,2817,2459765,00.asp
Read More:
DDoS Attack Puts Code Spaces Out of Business
Cloud code hosting service Code Spaces is forced to shut down, as a DDoS attack coupled with an unsuccessful extortion attempt was followed by the attacker deleting most of its code repositories and b…
View original post here:
Code hosting Code Spaces destroyed by extortion hack attack
The genealogy website Ancestry.com is working to fully restore its service after it was hit by a Distributed Denial of Service attack. Company spokeswoman Heather Erickson says it means ancestry.com was overwhelmed with bogus traffic Monday. “The attack was overloading our systems with massive amounts of traffic, but it did not access any data in servers,” Erickson said. The site, which has more than 2 million subscribers, was down for much of Tuesday and wasn’t fully operational Wednesday afternoon. Its Web team neutralized the DDoS attack and was working to fully restore services. “This has been a very frustrating and overwhelming experience, and our teams have been fantastic, working around the clock to make it neutralized,” Erickson said. Company officials are hoping to fully recover from the attack soon. Ancestry.com is posting updates on its Facebook and Twitter pages. Erickson said she doesn’t know where the attack came from. “These types of attacks aren’t unique to Ancestry. We know of many other companies that have been victim to these types of attacks. It’s unfortunate that any company has to go through something like this,” she said. The attack also impacted Ancestry.com’s sister site Find a Grave, though as of Wednesday afternoon it was back up, according to its Facebook page. Company officials said the sync and search feature in Family Tree Maker were still disabled until the site stability had been fully restored. They recommended people use the feature offline. Source: http://www.deseretnews.com/article/865605393/Ancestrycom-working-to-fully-restore-services-following-DDoS-attack.html
More:
Ancestry.com working to fully restore services following DDoS attack
Did dads storm site on Father’s Day? Some seem to think so The genealogy site Ancestry.com has been blasted off the internet after reportedly being hit by a DDoS attack.…
Read More:
YOU’RE HISTORY: Ancestry.com goes titsup for TWO DAYS
Earlier this week, Domino’s Pizza became the latest victim of a breach and ransom demand. Recent DDoS attacks on Evernote and Feedly DDoS, along with the efforts of Cryptolocker and other tricks to ex…
Visit link:
Five steps towards cyber breach preparation
Microsoft has released an update for its Malware Protection Engine to fix a privately reported security vulnerability that could allow a denial of service if the Microsoft Malware Protection Engine sc…
Follow this link:
Microsoft patches DoS flaw in its Malware Protection Engine

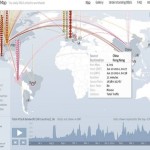 Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/
Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/
Read more here:
Hong Kong Voting Site Suffers DDoS Attack Before Civil Referendum
Although the GameOver Zeus botnet and CryptoLocker ransomware have been disrupted, it is still too early for a victory celebration. First, the two week deadline expires on June 17th, leaving just one …
View article:
Financial ransomware now targeting U.S. users